Asasin is rather an extension than an individual release of ransomware. This follows that of Ykcol, the latter is deemed to be eliminated from circulation. Both are the file extension that the victims find attached after the invasion of the Locky encryption plague. The latter, in its turn, has been around for a couple of years. In terms of crypto-extortion, the strain is a rare long-liver.
With .asasin intervention, there is a good chance for a victim to survive. Moreover, IT researchers claim getting the ransomware installed is a challenge. They say the crooks need both a spellchecker (hinting at the similarity of .asasin to the ominous word existing in English) and malware distribution skills. The current campaign that distributes the ransomware proves to be broken. It features a spam message with content attached. Luckily for the recipients, they cannot open the attachment. The hackers have uploaded it in such a way that the resulted message as seen by the reader shows no file attached.
Elbert Einstein once said, “Energy cannot be created or destroyed, it can only be changed from one form to another.” That is the case, the attachment dropped by the crooks remains within the message. Due to the awkward way it has been added, it appears within the body of the message. A sequence of base64 script represents the file, which the users are not likely to recognize as a content to load. Hopefully, the campaign fails already at this stage. Otherwise, there is another pitfall as the dropper goes packed with a rather unusual packer. There is a good chance the target system has no relevant software to unpack the dropper.
In the unlikely event of happy landing, the .asasin variant of Locky dropper reports to its remote server. The response will be the final downloader which installs the malicious encryptor.
The encryption goes beyond the file content as .asasin is the only readable part of the names of the files affected: the ransomware also encrypts the names of the files. The users are thus unable to tell one item from another and need to decrypt the names, too.
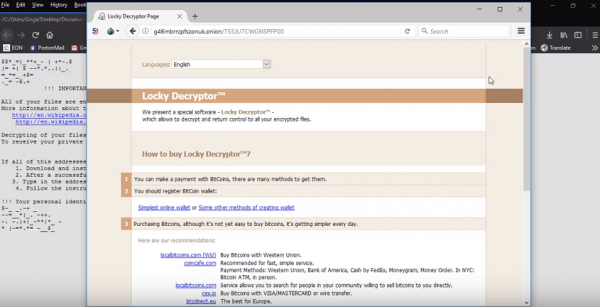
Removal of the encryption by .asasin is traded for some 0.25 BTC, which is currently around USD 1000. For that purpose, the infection drops a ransom note into every folder and the Desktop. It also tries to display it as a pop-up screen. The note says that Locky has encrypted your files with RSA and AES ciphers. To claim the encryption, the user is to contact the crooks. The follow-up is a predictable demand for the ransom in exchange for the decryptor.
There is no universal way to regain the data scrambled by the ransomware called .asasin with ransom-free workarounds. Try the methods outlined below and take care of regular backups, for prevention is the best cure.
Automatic removal of Asasin file virus
The benefits of using the automatic security suite to get rid of this infection are obvious: it scans the entire system and detects all potential fragments of the virus, so you are a few mouse clicks away from a complete fix.
- Download and install recommended malware security suite
- Select Start Computer Scan feature and wait until the utility comes up with the scan report. Proceed by clicking on the Fix Threats button, which will trigger a thorough removal process to address all the malware issues compromising your computer and your privacy.
Restore files locked by Asasin Ransomware
new Locky variant aka Asasin file virus represents a unique category of malicious software whose attack surface reaches beyond the operating system and its components, which is why removing the virus itself is a part of the fix only. As it has been mentioned, it encrypts one’s personal information, so the next phase of the overall remediation presupposes reinstating the files that will otherwise remain inaccessible.
-
Launch data recovery software
Similarly to the rest of its fellow-infections, Asasin Ransomware most likely follows an operational algorithm where it erases the original versions of the victim’s files and actually encrypts their copies. This peculiarity might make your day, because forensics-focused applications like Data Recovery Pro are capable of restoring the information that has been removed. As the virus further evolves, its modus operandi may be altered – in the meanwhile, go ahead and try this.
-
Take advantage of Volume Shadow Copy Service
This technique is based on using the native backup functionality that’s shipped with Windows operating system. Also referred to as Volume Snapshot Service (VSS), this feature makes regular backups of the user’s files and keeps their most recent versions as long as System Restore is on. Asasin file virus hasn’t been found to affect these copies therefore the restoration vector in question is strongly recommended. The two sub-sections below highlight the automatic and manual workflow.
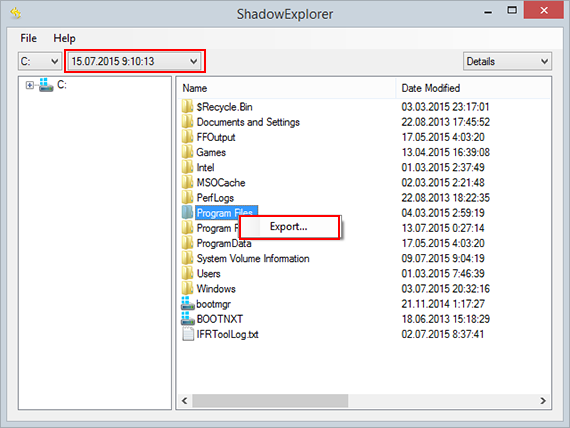
- a) Use Shadow Explorer
Shadow Explorer is an applet that provides an easy way of retrieving previous versions of files and folders. Its pro’s include an intuitive interface where the computer’s entire file hierarchy is displayed within one window. Just pick the hard disk volume, select the object or directory to be restored, right-click on it and choose Export. Follow the app’s prompts to get the job done.
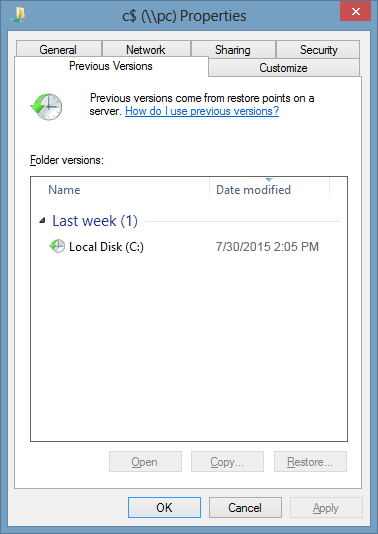
- b) Use file properties
Essentially, what the above-mentioned Shadow Explorer tool does is it automates the process that can otherwise be performed manually via the Properties dialog for individual files. This particular approach is more cumbrous but just as effective as its software-based counterpart, so you can proceed by right-clicking on a specific file, which has been encrypted by Asasin, and selecting Properties in the context menu. The tab named Previous Versions is the next thing to click – it displays available versions of the file by date of the snapshot creation. Pick the latest copy and complete the retrieval by following the prompts.
-
Data backups work wonders
Ransomware like Asasin isn’t nearly as almighty and destructive in case you run regular file backups to the cloud or external data media. The virus itself can be completely removed in a matter of minutes, and the distorted information can then be just as easily recovered from the backup. Luckily, this is a growing trend, so ransom Trojans are hopefully going to become less subversive in the near future.
Verify thoroughness of the removal
Having carried out the instructions above, add a finishing touch to the security procedure by running an additional computer scan to check for residual malware activity
